Introducing IOTA Access
IOTA Foundation and initial launch partners Jaguar Land Rover, STMicroelectronics, EDAG, RIDDLE&CODE, NTT DATA Romania, ETO GRUPPE and BiiLabs, announce global open-source framework for smart device access control able to manage billions of machines.
Update: IOTA Access is deprecated. With the Chrysalis network upgrade, the Access Core Software Development Kit isn’t actively updated anymore by the IOTA Foundation.
Today, we are excited to announce the launch of IOTA Access, an open-source distributed ledger technology framework for building policy-based access control systems and enabling pay-per-use functionalities at the edge. IOTA Access is designed to bring fine-grained access control to any machine, device, or building without relying on a centralized system or requiring a constant internet connection.
Access is all about enabling services and security at scale. If there’s a device that can offer a service, Access can be built into it to automate that service through embedded access control policies. This allows device users and owners to grant or request access to their device, or data stream, in a remote, permissionless, contactless, and auditable manner. Without decentralizing access control in an efficient peer-to-peer manner, we will continue to have our data, our devices, and our daily lives controlled by centralized institutions.
There is a necessary balance between decentralized technologies and semi-centralized management processes. Without this balance, trust in technology and how it is used in a global society is eroded. In the case of access control, we would have instances, where car owners get locked out of their own vehicles, and homeowners get locked out of their own homes. Key capabilities must be decentralized to ensure technology can be used for the betterment of humanity, in a trusted, secure, and open fashion.
With IOTA Access, the focus is to develop with an embedded first approach, in the smallest and lightest way possible, by allowing pay-per-use or access service models to be hardware-enforced. If you build solutions that function in the harshest, most resource-constrained environment first, then they can scale up to more robust environments with ease.
The new IOTA Access page is available for more information on how Access works, how to get involved, and how to work with IOTA Services to develop your own customized solution.
The use cases for something like IOTA Access are only limited by one’s imagination, but let’s lay out a foundation.
Zero trust at scale: Over the past 10 years, typical enterprise security frameworks have moved away from the old Trust Model for developing networks and enterprise solutions. Zero Trust Architecture, coined and created by John Kindervag in 2010 while he was at Forrester Research Inc., is now the primary direction for building secure architectures from the ground up. Zero trust architecture revolves around the model, “never trust, always verify.” Meaning that the way a system or solution is inherently designed needs to factor in that even trusted insiders in a network can be points of vulnerability. Insider threats exist. People make mistakes. And it only takes one to give rudimentary adversary access to an inner network. So security solutions must be designed in a way that factors in that risk, and segments access and permissions in a trustless way.
But the zero trust model is hard to scale, as it requires a high level of auditability and even harder, a high level of interoperability on a hardware and software level. Luckily, IOTA Access has that enabled in a lightweight, efficient, and open-source way. So as enterprises build out their zero trust integrations, IOTA Access can offer a utility to scaling those integrations to the edge of those networks and the devices they consist of. Whether that’s securing a secluded field sensor device through granular policy-based access controls, or securing offices and limiting access to only those with the proper clearance.
Just because IOTA Access enables pay-per-use services, doesn’t mean pay-per-use is required either. As always, the value transactions that occur on the IOTA Tangle are a function of the network, not a requirement to participate. So enterprises can enhance their previously centralized security solutions, with decentralized capabilities that scale better and reduce friction. All with transparency, immutability, encryption, and feeless data transfers. End users can have confidence that the security of the devices they’re integrating into their homes, cars, businesses and life can have heightened security, without the exorbitant costs that are often required, while taking back control of the devices they paid for and how they function.
The gig economy, minus the middlemen: The future is connected and smart devices are getting integrated into everything we come in contact with at an exponential rate. Whether you want to rent your house, bike, scooter, car or more, you could do it with IOTA Access. If you have a smart door lock, then it can integrate IOTA Access with embedded policies for pay-per-use rentals, or to simply increase the transparency and security of entering your home and allowing access to others. Signify your home is available on a decentralized marketplace, and anyone can find it and rent it. When they go to the door, the device already knows the cost and starts a payment stream. Microtransactions stream from your device to the home’s wallet in real-time, and when you leave that payment stops. Setting granular rates can happen at the edge. As long as the device can sync to the network, then the policies can update and stay on the device.
Have a connected vehicle that you want to rent out when you’re out of town? Wouldn’t it be great if you could leave it at the airport when you flew out, and someone getting off a plane could jump right in and pay you for using it? Or if your spouse, sibling, or friend could come to pick it up for you without you having to figure out what to do with the keys. Well, now that’s a possibility. Access is taking an initial focus on enabling services around mobility use cases, whether they’re micro-mobility, automotive, or other. You could rent your car for a few hours while you’re at work, or a few days while you’re out of town. You wouldn’t need to rely on a centralized service or middle man to facilitate the process. You choose your cost. You set the policy. You determine who has access, and when. The network and the vehicle do all the work. And don’t worry, you could even set rules for how your vehicle can be used along the way, and could even enable microservices for extra features like removing a speed limiter for the occasional thrill-seeker.
Wi-Fi without the worry: Alice runs a coffee shop and wants to provide Wi-Fi to her customers. What she doesn’t want is the cost, risk, and misuse of giving unrestricted access. But she also doesn’t want to hurt sales by offering an expensive, rigid subscription model from a telecom company. IOTA Access allows Alice to easily monetize her Wi-Fi, with no need for a subscription service managed by another organization. Her router can include a predefined Access Policy, like pay-per-minute or pay-per-megabyte, or she could also reward shop purchases with free access. The dashboard gives her an overview of usage and revenue and allows her to monitor the fair use policy in a GDPR-compliant way. That way she can decide to switch between payment models if needed. This helps her recoup costs, allows her to offer a better experience to her patrons, and enables her to focus on what she started the business for, a passion for making an excellent cup of coffee with a delicious scone on the side.
IOTA Access is established based on a depth of research on Access Control via Belnap Logic by Michael Huth (Imperial College London) and Glenn Bruns (Bell Labs). Initial prototypes were developed by XAIN AG, and they’ve graciously handed over the reins to foster its development and maturity to us at the IOTA Foundation who are currently working to further integrate this technology into the IOTA Protocol.
The combination of lightweight mathematically proven access control frameworks, embedded devices, immutable data, transparent audit trails, and feeless microtransactions opens up a wealth of capabilities that make the work that XAIN AG started a perfect match for the IOTA protocol. While also showing that layer 2 capabilities built on the IOTA protocol’s core are all about enabling new utility to decentralized ledger technologies because scale is already baked in and built-in fees should be a thing of the past.
As IOTA Access continues to be developed, integrations with other IOTA Products will be enabled, including enhanced automation and flexibility with Smart Contracts, secure secret sharing with IOTA Stronghold, and decentralized data streams sharing and monetization with IOTA Streams to provide completely automated access based on owner specified rules and restrictions.
To deep dive into the technical process, the new IOTA Access documentation page is also available. An overview of how IOTA Access works at a lower level continues below.
IOTA Access v0.1.0-alpha is released as a Minimum Viable Product (MVP) with a working implementation based on ARM Cortex-A running Embedded Linux (the famous Raspberry Pi 3/4). There are also planned efforts to have a working implementation running on STMicroelectronics SGP-TC-EVK Automotive Gateway Platform.
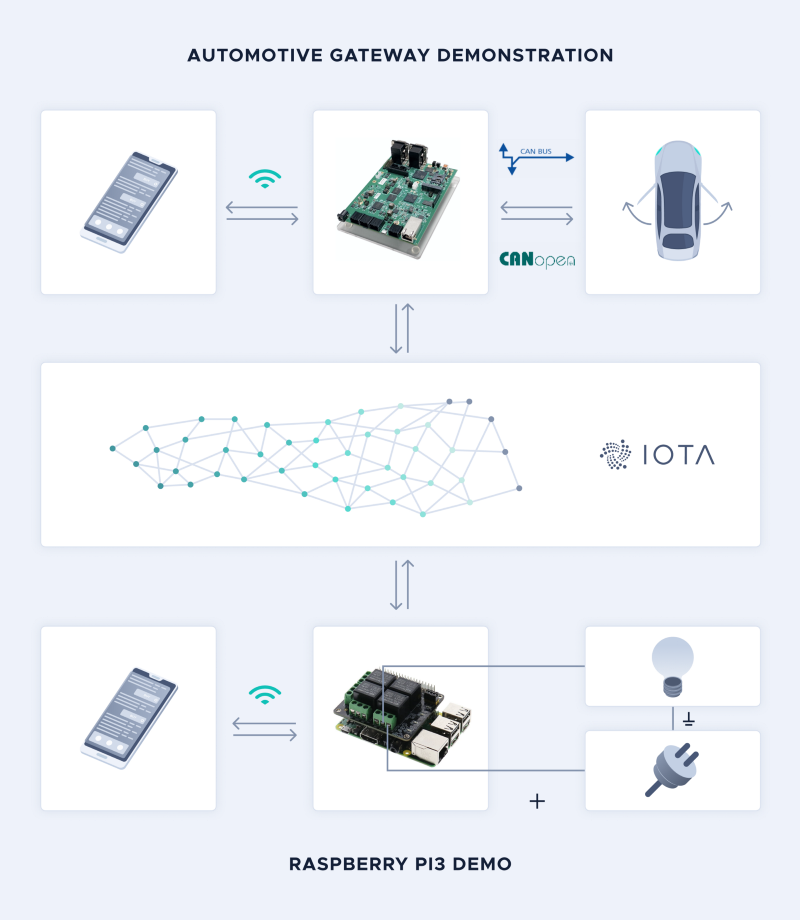
The IOTA Foundation positions itself at the forefront of Systems and Web Programming. As a reflection of that, the Rust programming language has been the choice for implementation of most of the IF products, due to its state-of-the-art features for memory-safe programming and easy pathways for rendering bindings to other languages like C, Python, WebAssembly, and others.
However, the drive for market adoption in the current state of the Internet of Things Industry has led to the decision of keeping the core of IOTA Access written in C. As a strategy, this ensures that ABI compatibility does not pose an obstacle for the integration of IOTA Access into popular microcontroller architectures.
Fortunately, Rust to C bindings are available via Foreign Function Interfaces. This allows Access to integrate tightly with the rest of the IOTA Products with near-to-null computational overhead. For every microcontroller architecture supported by the Rust compiler, IOTA Access libraries can be used in conjunction with every Rust crate from the IOTA Ecosystem.
IOTA Access is divided into a few repositories:
- github.com/iotaledger/access-sdk contains the Access Core Software Development Kit (SDK). It consists of the Core SDK components used as building pieces for Access dApps (server and client).
- github.com/iotaledger/access-server contains the Access Server Reference Implementation (ASRI). It consists of the embedded software executed on the target device for which access will be delegated.
- github.com/iotaledger/access-mobile-client contains an Android-based Access Reference Implementation. This is a demo user interface for creating policies and initiating access requests. It will eventually be replaced by the cross-platform implementation.
- github.com/iotaledger/access-policy-store contains the Access Policy Store. It consists of interface servers for managing policies. It will eventually be rendered obsolete when IOTA Chronicle is rolled out.
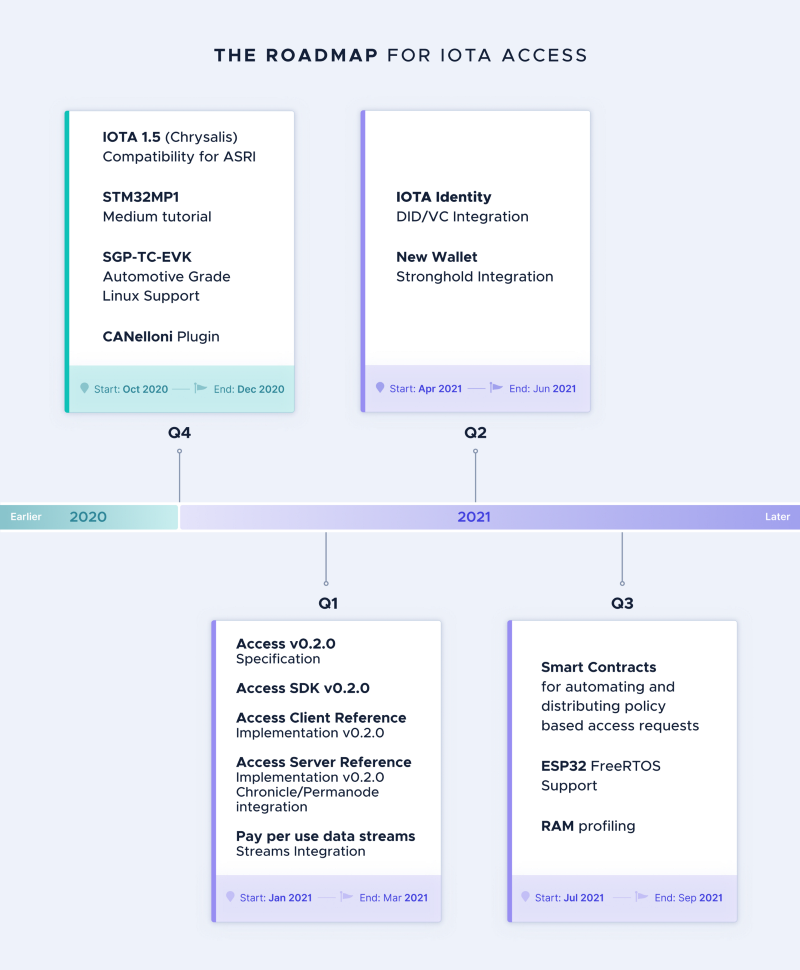
The following boards are on the Roadmap for hardware integration:
- Raspberry Pi 3/4: due to its popularity, the Raspberry Pi is used as the main platform for development. The initial v0.1.0-alpha release officially supports this board.
- STM32MP1: this development kit from IF partner STMicroelectronics is the perfect board for Yocto/OpenEmbedded integration of IOTA Access.
- SGP-TC-EVK: this development kit from STMicroelectronics will work as the PoC of Access on the Automotive Industry vertical.
- ESP32: the popular WiFi/BLE-enabled microcontroller will be used for FreeRTOS implementation of IOTA Access.
The possibilities are endless, but they’re just getting started. IOTA Access is now ready as an Alpha stage product to be further refined and developed through adherence to the IOTA Foundation’s dedication to open source and to enable the ever-growing and diverse IOTA ecosystem to test it and put it into practice. As the IOTA protocol continues to evolve, the products built on top of it offering layer 2 utilities will continue to be refined and progressed into Beta stages and full production readiness.
We thank our supporting partners for their valuable feedback and contributions in reviewing IOTA Access as an initial pre-alpha and their continued support moving forward as it continues to develop. We’re constantly looking for more partners and contributors to the project. You can directly reach out to us if you want to be part of this initiative.
Bernardo is leading the IOTA Access X-Team, to get started, discover the IOTA Experience Team on GitHub and apply through this form. We would also like to thank JKl2e (Johannes Kleeschulte) who contributed to the prototype Mobile Client.
The IOTA Community is welcome to contribute to the development of IOTA Access. The efforts during Q4 2020 will focus on making ASRI compatible with IOTA Chrysalis pt.2. Reviews and comments on the Access v0.2.0 specification are also welcome.
Authors: Mathew Yarger and Bernardo Araujo
As always, we welcome everyone to stop by on Discord to share your experience with this release!
Follow us on Twitter to keep track of all the latest news: https://twitter.com/iotatoken
For more information about the IOTA Access release: https://pr.slicedbrand.com/iota/access