IOTA Development Roadmap
IOTA was initiated with a very clear and focused vision of enabling the paradigm shift of the Internet of Things, Industry 4.0 and a trustless ‘On Demand Economy’ through establishing a de facto standardized ‘Ledger of Everything’. Since the very first lines of code was typed in middle of 2015 the project has come a long way, but in the big picture of this great journey IOTA development has only barely begun. This article unveils and outlines the IOTA Foundation’s public roadmap towards realizing this vision. This roadmap will be continuously updated in accordance with development progress and addition of new items. There are a lot of other stuff in the pipeline which will be added when ready to be unveiled.

The IOTA project’s number one priority is adoption in the real world. The foundation for achieving this lies in a deployment and development friendly ecosystem. This necessitates a versatile and vastly encompassing ecosystem, of which one of the most crucial components include clients in different languages that enable developers to choose their most preferred client suited for their specific deployments. We are currently working on:

The IOTA Reference Implementation (IRI) is written in Java. It has just been refactored with major performance improvements which makes it faster to synchronize with the network and make transactions. Since IRI is the first official IOTA implementation, a stable Java client is very much a key to adoption.

This client is our highest priority at the moment, as we are currently porting IRI over to C++ and plan to continue core development in this language. Unlike Java it does not require a Virtual Machine installed on the devices in order to to run code and it compiles to machine code in real time, making it a lot more suitable for these resource restrained IoT devices. It’s also one of the most supported and typed languages in the world.

Rust is considered to be one of the most promising and agile languages, particularly for IoT due to its safety, fast execution and massive concurrency support. Rust, together with C++, is currently being prioritized by the Foundation.

Very similar to Rust in terms of concurrency, Golang has seen a lot of adoption, especially by various Blockchian projects in this space. We already use Go for our Sandbox environment and library, making it an obvious choice to dedicate development to.


Even though IOTA core client is lightweight in nature, there are certain applications that need something even more bare bones.E.G. very resource restricted edge devices that will not be able to act as a full node, for these we have the Light Client. In addition to the Light Client, we will also offer an SPV-like client for trustless transactions and validation.

Another approach planned to enable the IOTA client running in these very resource restrained environments is to shard the core logic and database amongst different devices that then collectively run it. Similarly to swarm intelligence, this enables a cluster of devices to efficiently make transactions without being a full node, but having reduced trust requirements from SPV and light clients.



Because of the specific needs of networking for IoT, we have started the early research and development of a networking broker in IOTA that enables to fluidly switch between different networking protocols while still being connected to the peer to peer network. In addition to that, we will work on enabling peer discovery in a secure way.
To keep IOTA in accordance with the needs of embedded devices which will permeate and constitute the Internet of Things it uses ‘snapshotting’, which keeps the ledger database that devices has to keep very small in size. Snapshotting is similar to Blockchain pruning, except Snapshotting has the significant advantage of grouping several transfers to the same address into 1 record, which leads to a smaller storage requirement overall.
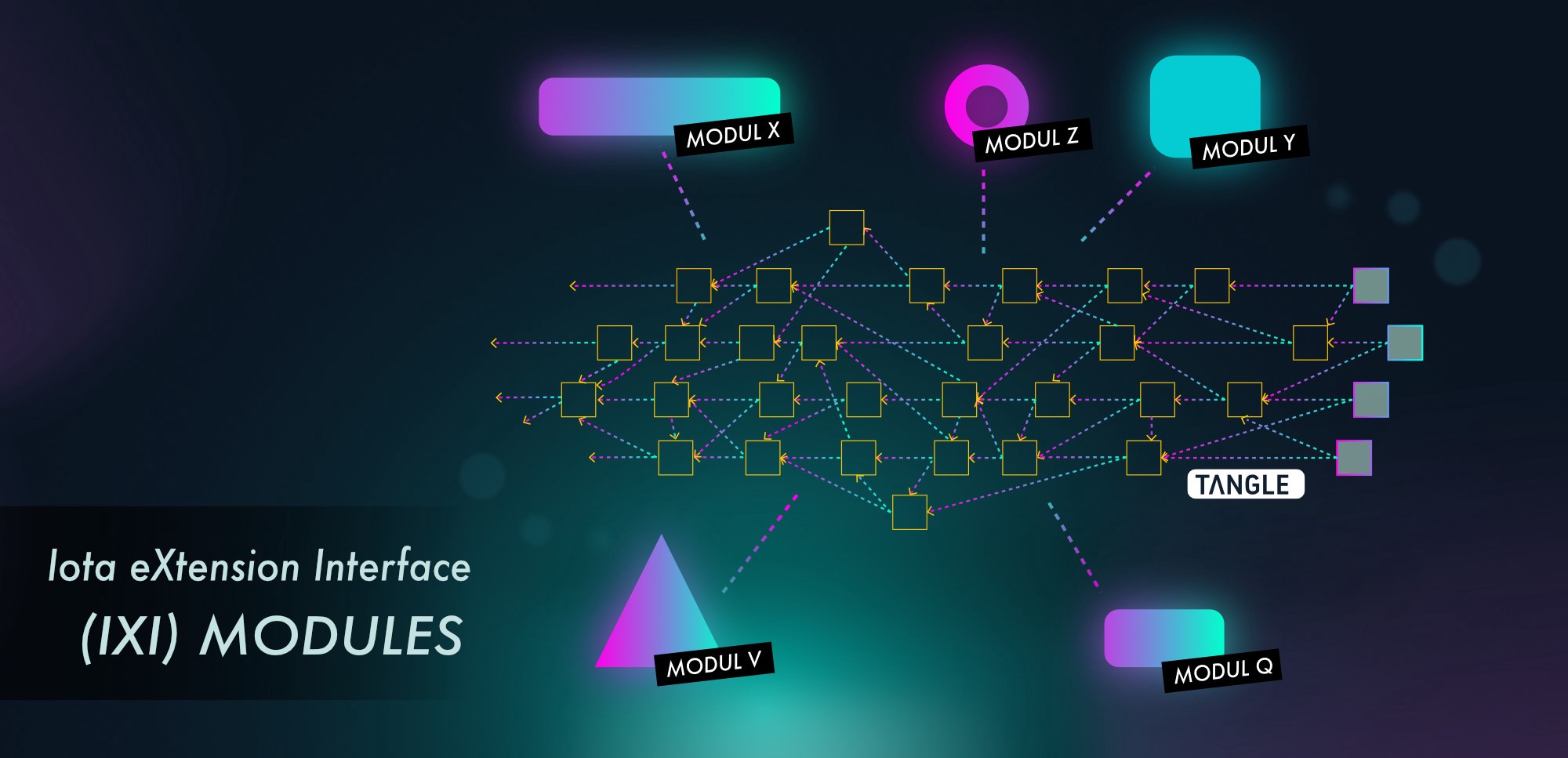
The core IOTA protocol itself is purposefully lightweight and simple in nature; its role is to enable trust free and fee-less transactional settlements as well as tamper proof data transmission. That’s it. Staying true to universal engineering principles we reduce trade-offs through the philosophy of modularity. Instead of creating a one size fits all swiss-army knife which invariably leads to mediocre performance in each feature, we instead make the IOTA platform modular. This means that each component is a stand alone application that is optimized for its purpose, without trading off performance or functionality for other applications. Additionally, this gives users of IOTA choice to tailor their usage of the protocol, instead of imposing the overhead of the features on, even if they originally only need to use one of them for instance. Both of these components are imperative for a scalable and functional platform.
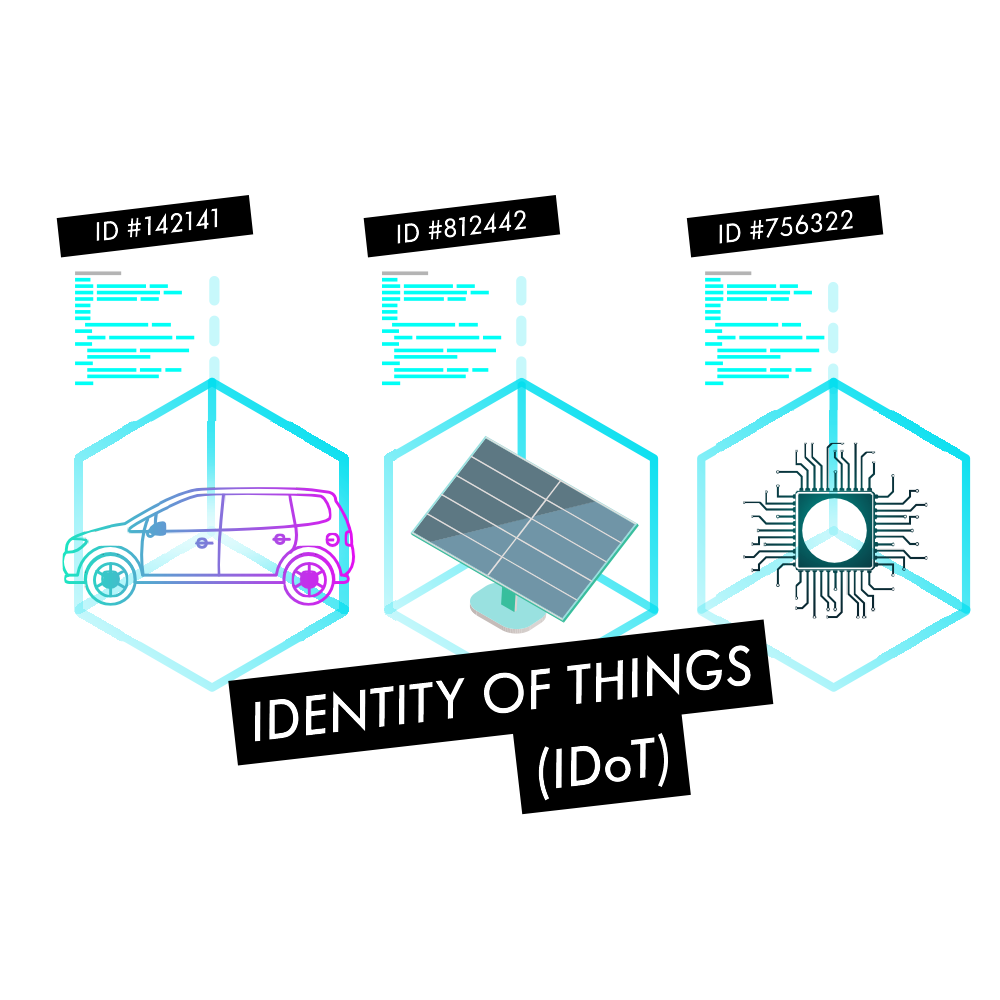
In order for IoT to securely mature into its full potential we have to fundamentally change how we think about machines/devices. Rather than perceiving them as lifeless amalgams of metal and plastic with a specific purpose, we need to shift toward considering each device as its own identity with different attributes.
For instance a sensor should not only have its unique identifier, but also accompanying it attributes such as: who manufactured it, when it was deployed, what is the expected life time cycle, who owns it now, what kind of sensor data is it gathering and at what granularity, does it sell the data and if so for how much? This is imperative for an efficient way to index and enable the Machine Economy and Industry 4.0 predictive maintenance. IDoT equally plays a vital role in securing the connected world. When each device has its own ID one can also establish reputation systems that are vital for anomaly and intrusion detection. By observing whether a device is acting in accordance with its ID or not, the latter which can be indicative of malware being spread, the neighbouring devices can quarantine it.
Status: At the present we are in the preliminary stages of researching and conducting ideation with developers and leading Industry and IoT actors on how such an identity system is to be comprised. It is vital that IDoT becomes a standard, as such input from as many as possible is a necessity. One thing is clear however: IOTA’s ledger will serve the role of ensuring that the device’s attributes and reputation is tamper-proof.
A future blogpost will delve deeper into IDoT.
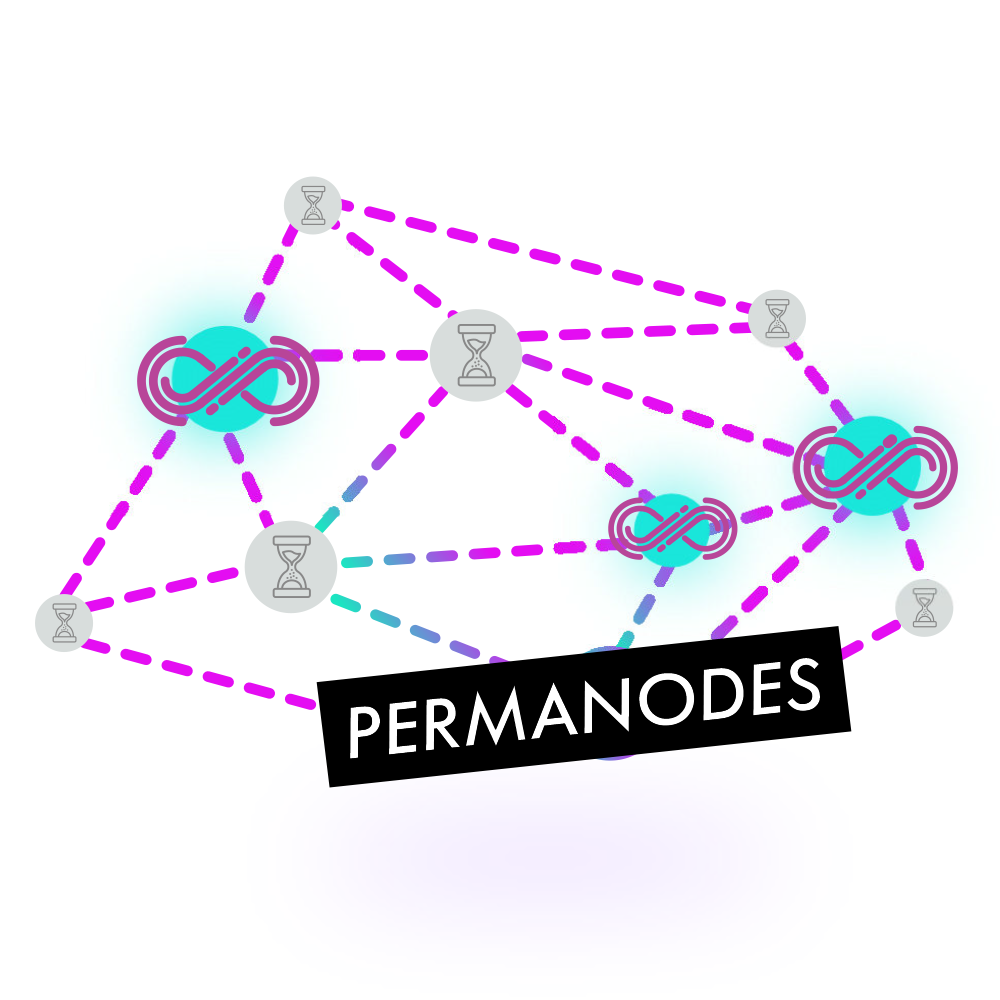
Since IOTA uses “snapshotting” to keep the size of the Tangle ledger database small, which is a prerequisite for IoT. This is all that is necessary for the vast majority of settlement and data integrity use cases. However, there are certain applications where the full raw data of the ledger has to be kept and be accessible permanently, for instance a transparent audit will require such an ability. This is the role of ‘Permanodes’. A Permanode stores the entire Tangle history and data in it permanently and securely. Through checkpointing in snapshots we make it possible to completely remove the trust requirements.

At the moment IOTA and IoT is in a early phase of what we consider to be a ‘transition period’ toward a production ready deployment and IoT environment. Until the network grows considerably, and beyond that the IoT landscape starts adopting DLT natively with hardware support, which will give IOTA for all practical purposes unlimited throughput, payment channels will serve a role for use-cases which require very rapid high throughput of transactions. The Flash Channels has clear benefits over similar initiatives such as Lightning and Raiden due to the unique Tangle architecture. These include no fees to setup channels, making it suitable for nano-transactions, as well as the fact that there are no miners in Tangle and thus no need to worry about transactions expiring before they are included into blocks.
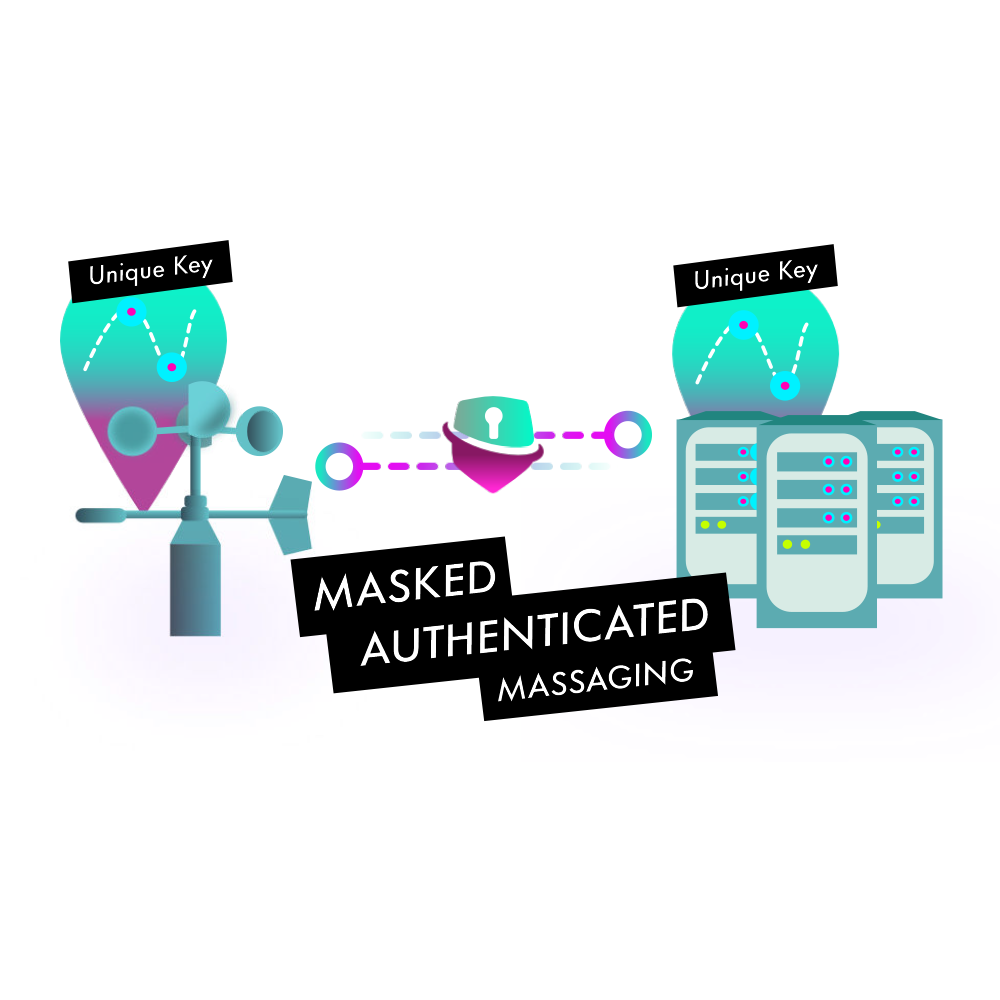
One of the most anticipated, and probably one of the most unique, modules for IOTA is Masked Authenticated Messaging. MAM makes it possible for sensors and other devices to encrypt entire data streams and securely anchor those into the IOTA Tangle in a quantum proof fashion. Only authorized parties will be able to read and reconstruct the entire data stream. In essence it works a lot like a radio where only those with the right frequency can listen in, in MAM only those with the right channel IDs get access to the data. You can expect many more announcements about MAM, as well as its applicability to industries such as Supply Chain, Banking and Industry 4.0.
Stage: Beta Testing

Just like MAM is providing security and privacy for data sharing, Private Transactions is there for transactional privacy. Transactions carry a lot of meta-information that reveal private information, this is amplified in certain IoT use cases, therefore a Private Transaction layer is in development. We will use token shuffling to achieve this in the first round, but are also exploring more extensive technologies such as zero knowledge proofs.

One of the main ways to extend the utility and applications of IOTA is through oracles. Through this one can feed outside data, such as timestamps, into the IOTA network. You can expect some exciting announcements here.

Any development ecosystem, in particular open source ones, depend on having a healthy pool of tools and libraries. Currently numerous of these are under development


The most widely used IOTA Library, the Javascript Library is largely the “reference” library for others, as it is the first to implement new features and make them available for developers. With complete API coverage, useful utility and wrapper functions and full multisignature support, the Javascript library makes it incredibly easy to make use of IOTA for your NodeJS and Browser applications.
Status: Done
Probably the most popular prototyping language, the Python Library (called PyOTA), is largely feature complete and is only awaiting for Multisignature support to be fully tested. PyOTA has already been used by several of our Proof of Concepts and even Hackathons.
Stage: Completed, with further improvements soon


The Java Library, which is being used by the Android mobile wallet in the current test phase, has been developed and is largely feature-complete. All of the functionality and wrapper functions from the Javasctipt library are ported to Java, with full test coverage. Multi-signatures support is already implemented and is currently being security reviewed.
Stage: Completed
Similarly to the Java library, the C# Library is feature-complete and has most of the API functionality from the Javascript library implemented. We expect to add multi-signature and optional key security for addresses and accounts in an upcoming release.
Stage: Completed, multi-signatures soon

The Go Library, which is actively being used by our Sandbox developer environment, is being actively developed by two of our developers and will be ready for public testing in April. We’ve also provided a simple CLI.
Status: In development


In order to showcase the capabilities of the IOTA Tangle ledger in terms of being the most scalable public distributed ledger with the highest throughput, as well as see that the network topology indeed can sustain itself, we are planning numerous different kinds of stresstesting that will take into account computational power, user load, latency of distributed nodes etc. You can expect more information and announcements with some of our partners about this soon.
Stage: Planning and preparation

Considering that the Tangle is such a radically new concept, which is often difficult for some to comprehend and fully understand, we’ve been working on a simulation framework in Python for the last months. This simulation framework will make it possible to simulate cluster and network settings, transaction finality times, transaction propagation, different tip selection strategies and the overall confirmation rates. In addition to that, we’ve implemented the attacks (as mentioned in the whitepaper), so you can visually see how the Tangle is able to sustain such attacks.
Status: Largely completed, awaiting peer review

Empowering developers means reducing the entry barrier, which our Sandbox is taking care of. The IOTA Sandbox makes it incredibly easy for developers to “just code”. You don’t have to worry about downloading any software, setting up your local environment or anything else. We take care of all the heavy-lifting for you, we even do the Proof of Work for you with our dedicated GPU’s. After a short break, we will continue operation of the Sandbox environment in mid April.

Fueling the application development around IOTA is our main priority. As one of the first major community efforts, we’ve setup IOTA Learn as a central repository of all the relevant developers tutorials, code snippets and resources. Not only does this make it easy for developers to quickly dive into IOTA and learn from experts in the community, but they can even become the teachers themselves and have their projects and tutorials featured on the homepage.
Stage: Check it out!
The IOTA ecosystem is growing every day, with new developers, researchers, NGOs, startups and large corporates coming together to explore what IOTA and the Foundation offers to further fuel new applications, social impact and business opportunities. With such an ambitious and comprehensive roadmap, we are positioning IOTA as one of the most unique and respected solution providers in the space. Expect a lot of exciting development and ecosystem announcements in the following weeks. IOTA started as a grassroots effort and is still very much a completely open source public project. We invite everyone to partake in the ecosystem, join us on Slack, follow us on Twitter, or subscribe to our newsletter.