IOTA Hierarchies Alpha is Live
Flexible and Verifiable Trust Networks
TL;DR:
IOTA Hierarchies is an open-source product for cryptographically verifiable trust delegation across people, organizations, and devices. It allows entities to define a set of properties, delegate authority, and validate trust relations both on- and offchain. Now released in Alpha, IOTA Hierarchies provides a scalable, industry-agnostic way to model who is trusted, for what, and by whom, enabling secure, transparent, and revocable credential verification across sectors.
In a digital world, we form relationships based on trust on a daily basis. Regulators trust auditors, companies trust suppliers, and systems trust devices. But the logic behind these trust relationships is often hidden, informal, or locked in organizational silos.
This leads to a range of problems, particularly for collaborative digital environments. These include:
- Trust is assumed rather than explicitly verified.
- Credentials are issued manually, often without a standard format or digital verifiability.
- Authority is delegated informally, making it difficult to trace and almost impossible to audit.
- Decisions can’t be automated because there’s no standard way to express and validate them.
While decentralized identity tools can help prove who you are, they regularly don’t answer a deeper question: why should I trust you?
Solving the Trust Problem with Onchain Delegation
IOTA Hierarchies, a new product developed by the IOTA Foundation, solves the problem of unstructured and ambiguous trust by enabling clear, transparent, and revocable delegations of authority on a distributed ledger. This makes trust explicit and auditable, replacing informal assumptions with clear, verifiable logic.
IOTA Hierarchies is a free and open-source library designed to model trust across all key identity types involved in digital systems, both onchain and offchain:
- People: Individuals who hold credentials or perform trusted actions.
- Organizations: Legal entities that define policies and delegate authority.
- Things: Devices that interact autonomously and require verifiable trust.
This enables end-to-end, programmable trust flows, whether for manual processes or automated systems.
IOTA Hierarchies runs on the IOTA Mainnet, Testnet, and Devnet. It integrates with IOTA Identity but can also operate independently. Finally, it's flexible and non-opinionated, meaning it doesn’t enforce a specific trust model but allows each ecosystem to define its own trust logic.
The result is a trust model that is verifiable, auditable, and ready for real-world applications. Trust becomes explicit and reusable across systems.
Industry Applications
Thanks to its general-purpose design, IOTA Hierarchies fits use cases across sectors, such as:
- Education: Universities can delegate diploma issuance to departments and professors, enabling verifiable academic credentials.
- Supply Chain: Trusted entities can certify products at each step. Attestations like quality checks are only accepted if issued by accredited parties.
- Legal and Compliance: Governments can accredit notaries and auditors, creating verifiable chains of authority for documents and reports.
- Government: National authorities can delegate powers to local officials, and then citizens can verify that permits or certificates were issued legitimately.
- IoT and Automation: Devices can verify commands and data based on accredited trust chains, enabling scalable and secure machine-to-machine interactions.
In all these cases, IOTA Hierarchies provide the backbone for decentralized trust management, defining who is trusted to do what, in a formal and shareable way.
Importantly, this extends beyond identity. Any action or data point that requires trust, such as issuing a verifiable credential, signing a document, approving a transaction, validating sensor data, or assigning access permissions, can be represented in the framework.
Core Concepts and How They Work
IOTA Hierarchies provides a structure for defining, delegating, and verifying trust between entities. Instead of relying on assumptions or central gatekeepers, this model uses cryptographic links to express who is trusted, for what, and by whom.
The system is based on a set of building blocks that together form a verifiable chain of trust:
- Federation: A collection of entities operating under shared rules and that defines the trust domain. Each federation is created and managed by a root authority and contains the definitions of roles and properties that can be assigned and delegated.
- Root Authority: The initiator of the trust network. It defines properties and delegates authority by issuing accreditations to other entities. It holds the power to approve or revoke permissions within the federation.
- Statement: A role, permission, or attribute that can be assigned to an entity. Examples include permission to issue grades, verify compliance, or certify a product. Properties may also include constraints to define valid scopes of use.
- Accreditation: A cryptographic delegation that grants an entity the right to attest or accredit a specific statement. Accreditations connect each entity to the trust chain and define what it is allowed to do within the federation.
- Attestation: The result of delegated authority. It is a signed statement confirming a trusted property. Attestations can be onchain or offchain and are always verifiable against the originating accreditation.
- Value & Conditions: Optional conditions that limit how a property can be used. They define valid values or patterns, ensuring that roles are applied within safe and expected boundaries.
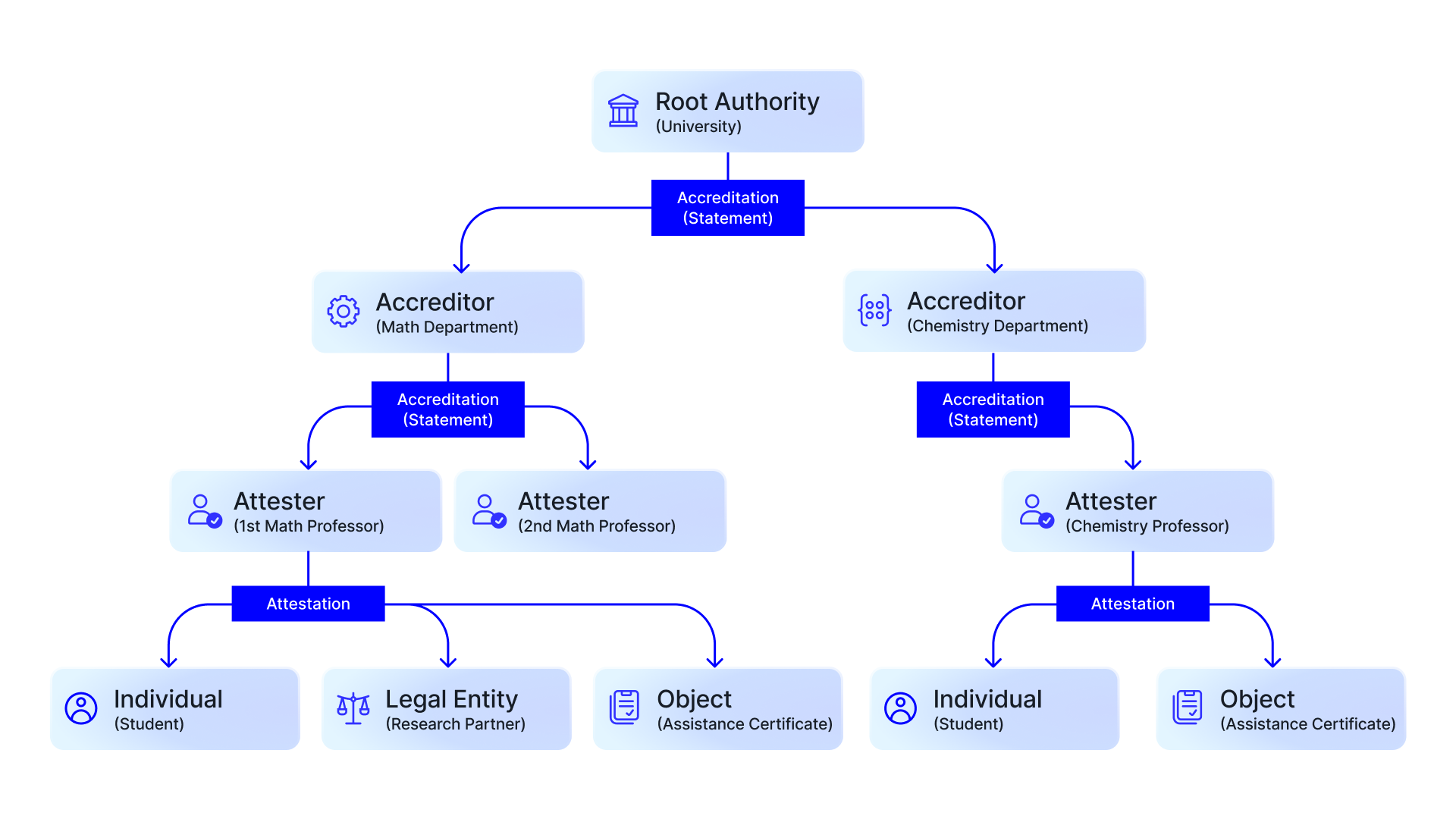
In this example, the University acts as the Root Authority, initiating the Federation and defining which departments are trusted to issue specific types of credentials. It grants accreditation statements to the Math and Chemistry Departments, designating them as Accreditors. Each department can then delegate authority further, for instance, by accrediting specific Professors as Attesters. Once accredited, these professors can issue attestations – verifiable statements – to different types of entities. A Math Professor might attest to a Student’s successful course completion, a Research Partner’s involvement in a project, or the issuance of an assistance certificate for a particular academic activity.
Validation Modes
Once recorded, the trust data can be validated in two ways:
- Fee-Based Validation: Executed through smart contract calls on the IOTA network. This method ensures full onchain execution, offering maximum transparency and decentralization. Ideal for public or regulated environments and when another smart contract needs to directly act on the verification result.
- Feeless Validation: Handled by the client library, which interacts directly with a Node API to execute the same validation logic without paying transaction fees. This is optimal for fast, private, and low-cost scenarios.
Developers can combine these two approaches to strike the right balance between cost, privacy, and auditability.
Get Started
Explore these resources to begin using IOTA Hierarchies:
- GitHub Repository: Contribute and access open-source code.
- Builders Discord: Engage with the developer community.
- IOTA Docs: Comprehensive setup guides, best practices, and APIs.
- Rust Library & SDKs: Install libraries for smooth integration.
Tracing Trust to the Source
In a decentralized world, trust must be explicit, verifiable, and programmable. IOTA Hierarchies deliver a practical foundation for building transparent, scalable trust relationships across industries, devices, and identities.
Whether you’re enabling decentralized credentials, authorizing IoT devices, or delegating institutional roles, IOTA Hierarchies provide the infrastructure to model trust the way the real world works. Structured, revocable, and shareable.




