Official IOTA Foundation Response to the Digital Currency Initiative at the MIT Media Lab — Part 2 / 4
The IOTA Foundation no longer supports or endorses this article. We have however kept it available for transparency purposes.
Editor’s Note:
All of the information and links contained in this multi-part document were publicly available prior to publication. None of the information contained herein is new or revelatory.
This is a collective effort by many members of the IOTA Foundation and IOTA Core team. The purpose of this aggregation is to add color and context to these complicated and multi-faceted issues, so that the entire Distributed Ledger Technology (DLT) community can decide the relevance of this information for themselves.
In early September of 2017, the DCI team posted an IOTA Vulnerability Reportand accompanying blog post purporting to describe a number of flaws in various aspects of IOTA’s technological underpinnings, including the method of providing “digital signatures” for IOTA (the Curl-P hash function), network stability, and possible attack vectors (e.g. double spending, theft, or signature forgery). Because the DCI falls under the umbrella of the well-respected Massachusetts Institute of Technology (MIT), the general public unwittingly sees DCI as a formidable academic institution — this despite being only loosely connected to the university and having published very little peer-reviewed academic work. This is evident from news outlets and blog posts describing the DCI report as being that of “MIT” and, as a result, misinformation has been circulating in the DLT community for many months now, despite repeated attempts by the IOTA team to correct these falsehoods.
Security is the IOTA Foundation’s top priority, and as such we have taken the findings of this report very seriously. We have given, and will continue to give all due consideration to investigating the veracity of, and responding to such concerns. In the case of this report, the IOTA team has worked tirelessly since September to respond to the questions raised, and to demonstrate both the security of the IOTA protocol and of the Tangle.
A few examples:
- Sergey Ivancheglo’s email correspondence and follow-up to the DCI Report (July — September, 2017)
- David Sønstebø’s initial response to the DCI Report (September 7, 2017)
- Sergey’s response to a community member on Reddit (October, 2017)
Earlier this month, the MIT Technology Review (a separate entity under the MIT umbrella, also only loosely connected to the school) posted a positive review of IOTA, to which the DCI team responded with another set of ongoing concerns. This new post reiterated many of the same concerns as their initial report — concerns which the IOTA team had already addressed (see links in the bullet points above).
Additionally, the new DCI post called into question the IOTA Foundation’s honesty regarding corporate partnerships and claims of “feeless” transactions. These concerns have also been addressed:
- Dominik Schiener’s response to a TNW article questioning the relationship between IOTA and Microsoft (December 16, 2017)
- In the original IOTA white paper it states, “ … in IOTA the number of nonces that one needs to check in order to find a suitable hash for issuing a transaction is not unreasonably large. On average, it is around 3⁸.” As we will discuss in Part 3 of this article, this entails that transactions are effectively “feeless” under any reasonable interpretation.
Over the last few months the IOTA Foundation has been extraordinarily busy working to improve our technology, to build meaningful relationships with major corporations around the world, and to successfully launch our first large-scale collaborative platform, the IOTA Data Marketplace. The articles posted during this period by the DCI team have done little but sow confusion within the IOTA community and the broader DLT space.
We take full responsibility for allowing this thorn in our side to fester for so long, and we feel it is necessary to put forward an official and comprehensive response to put these questions to rest.
Ordinarily, a party intending to responsibly disclose a vulnerability discovered in an ongoing project will directly contact the project developers. An embargo period is instituted, during which the vulnerability is not discussed with non-involved third parties, allowing time for the vulnerability to be patched. This is essential in cases where it could help prevent the loss of unwitting parties’ funds. At the end of the embargo period, the vulnerability information is released to the public.
In this case however, the IOTA team were directly contacted by other members of the DLT community during this embargo period, saying that they had heard about this “vulnerability”. This raises concerns regarding the confidentiality of the disclosure process. Given the claimed impact by DCI, either they did not responsibly disclose their findings (reportedly “putting billions at risk”) or they did not believe their “vulnerability” posed any real threat. As outlined in Sergey Ivancheglo’s final email to the team:
— — — — — — — — — — — — — — —
7th of September
— — — — — — — — — — — — — — —
Hi Neha,
I think if your team fixes all issues in Ethan’s findings there will be nothing to publish left. 1 day is not enough for you to extend the “attacks” to something possible in practice, so let’s just continue our dispute in public.
I’m still expecting to get an explanation of how a RESPONSIBLE disclosure led to numerous people outside of our teams knowing the details before the update was even scheduled……
…..Personally, I just can’t get if you were knowing from the very beginning that the “vulnerability” found by Ethan wasn’t critical or that your disclosure wasn’t actually responsible given how many independent people, most of whom are not cryptographers or security researchers, has reached out to us about it (and that was only a part of those who had known about Ethan’s findings).
…..Personally, I just can’t get if you were knowing from the very beginning that the “vulnerability” found by Ethan wasn’t critical or that your disclosure wasn’t actually responsible given how many independent people, most of whom are not cryptographers or security researchers, has reached out to us about it (and that was only a part of those who had known about Ethan’s findings).
There was no response to this email.
Moreover, in academic circles it is standard procedure for cryptographic vulnerability to be independently audited, verified by the academic community, and published in academic papers to allow for peer-review. In this case, the vulnerability report was published as a non-peer-reviewed blog post and Github upload, despite touting the academic affiliation of the MIT Media Lab DCI team. In the blog post, the DCI team promised that a full report and code release would follow. Several months later, after repeated requests from the IOTA team, the DCI team has still not released any exploit code publicly.
This is unfortunate, as it means neither the IOTA team nor any independent third party has been able to verify the claims made in the blog post. The code uploaded to Github at the time of the blog post merely illustrates how an exploit might be carried out once a suitable attack target has been identified. It does not indicate, however, how suitable attack targets might be identified so as to make a “practical attack” as claimed in the blog post, rather than merely a theoretical one. Despite these shortcomings, media coverage of the report frequently promoted the blog post under the MIT name, thereby suggesting that the post should nevertheless carry the full validity that would ordinarily be conferred by an MIT academic imprimatur.
Given that many of the claims leveled against IOTA are at best unintentionally misleading, and at worst, purposefully so, we are compelled to ask why, given the hundreds of projects in the DLT space making all sorts of questionable design decisions and even perpetrating outright frauds, there has been so much concerted effort on discrediting our particular project. While our primary focus is and always will be on the technology behind IOTA, we would be negligent if we did not at least do our “due diligence” in the form of opposition research. We offer three possibilities that we feel are worth consideration:
- IOTA is unique in that there are no fees for miners of any kind. This fact threatens the business model of companies that have made significant capital investments into, for example, mining farms which cannot be easily repurposed to other valuable uses outside of mining PoW DLT protocols.
- Many DLT protocols have specific-use, utility style tokens. Our goals for IOTA — to be a truly distributed, permissionless, fee-free, and near-instant protocol for general value and data transfer — threaten some of the most successful tokens currently on the market.
- In addition to the general disruptiveness IOTA may bring to the DLT space as a whole, many of the people behind the articles and criticisms discussed above would be personally affected by the success of the IOTA project.
There are some apparent Conflicts of Interest (COI) regarding the Media Lab as an institution, as can be seen here and here.
More specifically, many of the people at DCI who were directly responsible for much of the controversy surrounding IOTA in the last few months have significant, personal COI due to their involvement in competing technologies. Given that DCI falls under the MIT umbrella (even if only on its periphery), their opinions have been given significant weight and as such, their COIs should be subject to equally significant scrutiny, which we lay out in detail below.
Neha Narula & Tadge Dryja
Neha Narula, DCI Director, is playing an active role supporting Bitcoin’s development of the Lightning Network, a proposed / experimental solution for fast and inexpensive off-chain transactions to solve Bitcoin’s problem of slow and costly on-chain transactions.
Tadge Dryja, co-author of the Lightning Network white paper, was recently hired by DCI. Neha and Tadge appear to be heavily involved in the development of a competing technology which hopes to offer fast and near-free transactions and are also both co-authors of the “Cryptographic Vulnerabilities in IOTA” blog post.
Madars Virza
Madars Virza, DCI researcher and co-author of the IOTA vulnerability report, is also a co-author of the Zerocash white paper, and is part of the leadership behind the cryptocurrency protocol Zcash, a cryptocurrency with a $1.5 Billion market cap at the time of this writing. Zcash, through zero-knowledge proofs, claims to solve problems of true anonymity in Bitcoin. Recall that Neha’s blog post criticizing IOTA’s cryptography said:
The golden rule of cryptographic systems is “don’t roll your own crypto.” If asked, any security researcher will tell you to only use well-understood and well-tested cryptographic primitives when building a system.
…
So when we noticed that the IOTA developers had written their own hash function, it was a huge red flag. It should probably have been a huge red flag for anyone involved with IOTA.
So when we noticed that the IOTA developers had written their own hash function, it was a huge red flag. It should probably have been a huge red flag for anyone involved with IOTA.
Yet, Zcash also “rolled their own crypto”, a fact which was well-covered in DLT media. Oddly, this hasn’t raised any red flags or comprehensive investigations into Zcash’s own cryptography, or blog posts from DCI with statements such as, “Please don’t roll your own crypto” and, “Large organizations and well-known individuals should not lend their names and reputation to technology they have not vetted.”
Ethan Heilman
Ethan Heilman, Partner at DCI and lead author of the IOTA vulnerability report, is also part of the leadership atDAGLabs, a for-profit company based in California that is working to build their own DAG-based protocol based on the SPECTRE white paper. As IOTA is the current de facto leader in DAG-based DLT protocols, comparisons are often drawn between the two protocol designs because SPECTRE also claims to enable unlimited transaction scalability. Around the time when this vulnerability report was published, DAGLabs was in the middle of a Series-A financing round. At the very least, the vulnerability report was published at a very convenient time for DAGLabs.
The IOTA team has been aware of Ethan’s expertise in the space for some time, and reached out to him personally as far back as May 2017 to ask for a technical audit of IOTA’s code. At that time he disclosed that he was undertaking similar research, which may result in a conflict of interest. From our point of view, this brings up a serious question. If there was a potential conflict of interest then, how is it possible that he could objectively review IOTA’s code soon after while being a member of the leadership team at a direct competitor going through a major round of fundraising?
Joichi Ito
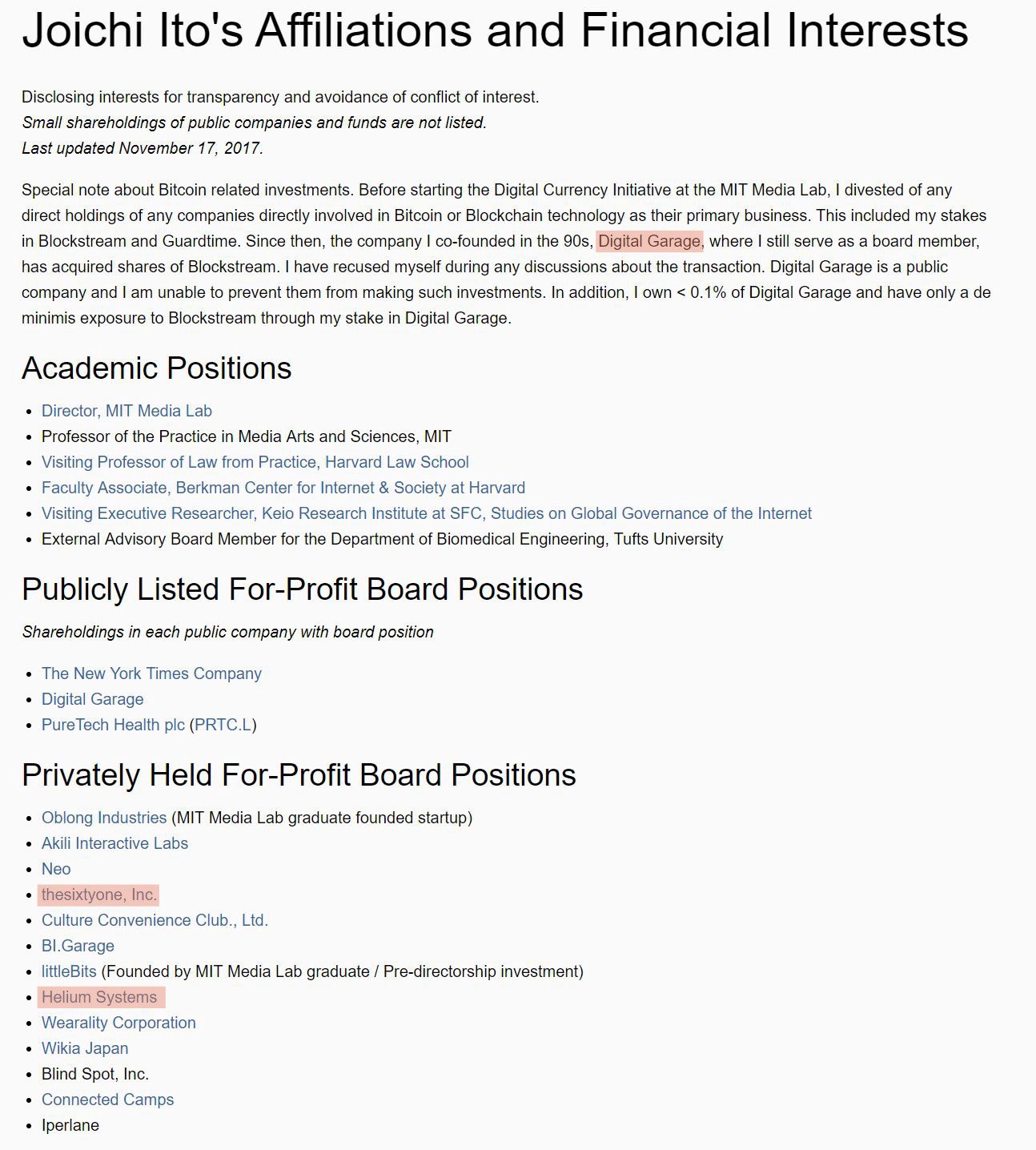
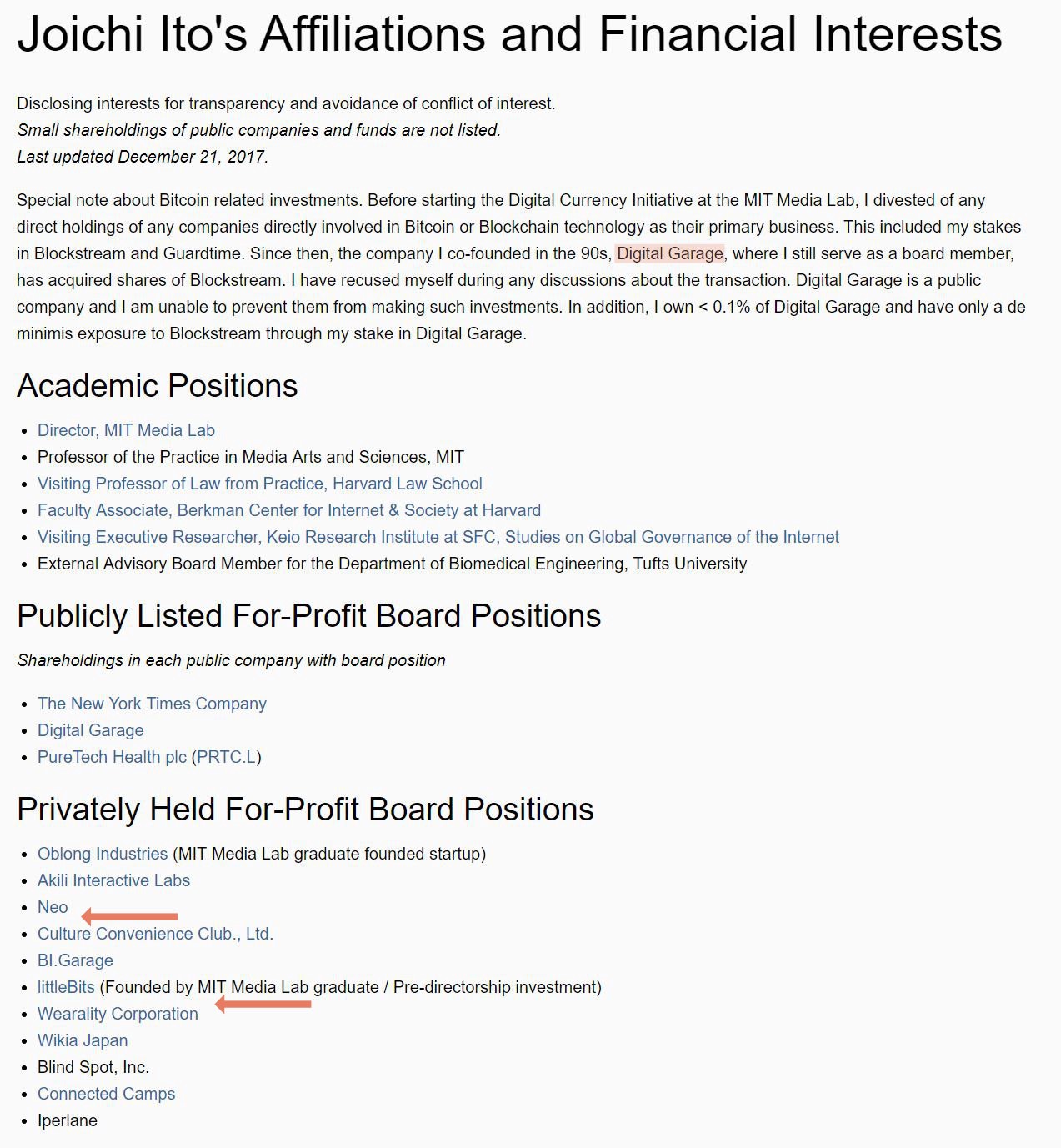
Joichi Ito, Director of the MIT Media Lab, authored the most recent critical article on IOTA published by DCI. Curiously, Joichi’s personal COI disclosure pagewas updated immediately following publication of his article (published on December 20th, COI disclosure page updated on December 21st. Before/After). Using the Wayback Machine, we can see that with this update, Joichi removed two privately held for-profit board positions, Helium Systems and thesixtyone, Inc. thesixtyone does not appear to be relevant. Helium Systems, however, according to theirwebsite, “provides robust and secure IoT device connectivity for a fraction of the cost of our competitors.” As the IOTA Data Marketplace blog postexplains, IOTA aims to displace exactly such business models where data is siloed into proprietary cloud databases. The success of IOTA would be at the very least disrupting to a company like Helium.
We do not know whether there is any connection between the publishing of this critical article on IOTA and the update to Joichi’s COI disclosure page just one day later. Helium Systems, for its part, still lists Joichi as the company’s board director at the time of this writing. Regardless, Joichi, according to his disclosure page, still holds Helium Systems stock and/or options.
In addition, Joichi asserts at the bottom of this critical article, “He doesn’t add[sic] a material amount of any crypto currency or shares in any crypto currency companies.” To his credit, Joichi links to his COI page, but what it reveals is that he still holds stock in Digital Garage, a company which he founded and which is very much a “crypto currency company” having made an investment in Blockstream, the self described “leader in blockchain technologies and financial cryptography” in November of 2017. Digital Garage has a market cap of over $1 Billion at the time of this writing. While Joichi claims to own less than 0.1%, this allows him to own up to $1 Million worth — an amount which most reasonable people would consider to be a very material investment.
So even though Joichi seems to be professing impartiality in his article, the evidence above suggests this may not be the case. One would think that with such obvious COIs, he should make these financial interests in competing technologies manifestly apparent to the reader, as required of faculty and staff at MIT (see MIT Policies & Procedures Section 4.4).
In our next article of this mini-series, we will start to discuss in detail each of the points raised in the DCI’s reports and examine the deeper, underlying issues.
This is a multi-part post. Links to the other parts can be found below:
Part 1
Part 2 (this article)
Part 3
Part 4