Official IOTA Foundation Response to the Digital Currency Initiative at the MIT Media Lab — Part 3 / 4
The IOTA Foundation no longer supports or endorses this article. We have however kept it available for transparency purposes.
Editor’s Note:
All of the information and links contained in this multi-part document were publicly available prior to publication. None of the information contained herein is new or revelatory.
This is a collective effort by many members of the IOTA Foundation and IOTA Core team. The purpose of this aggregation is to add color and context to these complicated and multi-faceted issues, so that the entire Distributed Ledger Technology (DLT) community can decide the relevance of this information for themselves.
In what follows, quotes from Joichi Ito’s criticism of IOTA are shown at the start of each section, followed by the response of The IOTA Foundation.
DCI’s claim:
“IOTA’s relationships with top-tier companies continue to be nebulous.
In the Technology Review article, Orcutt linked to a November 28, 2017 blog post from IOTA that gave the perception that Microsoft was a partner in the marketplace. However, after a flurry of media reports making this claim, IOTA corrected their relationship status with top-tier companies like Microsoft, Cisco, and Huawei in a blog post dated December 16. That the MIT Tech Review story links to IOTA’s initial blog post instead of the later version is misleading.”
In the Technology Review article, Orcutt linked to a November 28, 2017 blog post from IOTA that gave the perception that Microsoft was a partner in the marketplace. However, after a flurry of media reports making this claim, IOTA corrected their relationship status with top-tier companies like Microsoft, Cisco, and Huawei in a blog post dated December 16. That the MIT Tech Review story links to IOTA’s initial blog post instead of the later version is misleading.”
Here is the section in question, quoted directly from the press release:
“ Over the next few weeks the IOTA Foundation will publish several blog posts, case studies, and opinion pieces together with chosen partners to elaborate on future applications of the data marketplace for specific industries.”
(Emphasis added.)
“ Over the next few weeks the IOTA Foundation will publish several blog posts, case studies, and opinion pieces together with chosen partners to elaborate on future applications of the data marketplace for specific industries.”
(Emphasis added.)
We do not find this usage of the word “partner” to be in any way nebulous. In the statement, we are referring to a subset of IOTA Data Marketplace participants with whom we are actively working to deepen our level of collaboration. Apart from this paragraph, all other uses of the word “partner” were by three of the participants themselves, including a Microsoft representative. We used the participants’ quotes only after seeking permission from them, and we have a full correspondence trail to support this. We believe we have followed the correct due process, as Dominik Schiener detailed in our clarification of the incident.
To be absolutely clear: at no point was a formal corporate partnership implied either directly or indirectly in any post, statement, or press release issued by the IOTA Foundation.
While we do not believe that any of the above statements were inaccurate or misrepresented the project in any way, we fully understand and are empathetic to the fact that some of the reporting in the media was inaccurate and ultimately the buck stops with us. In hindsight, we should have taken even greater precautions with these companies to ensure that the press release we authored, and the statements they provided us, followed a rigorous internal approval process on their end. However, the suggestion that the IOTA Foundation purposefully allowed these misrepresentations to persist could not be further from the truth.
As soon as we became aware of the inaccurate reporting (which in addition to the inaccuracies mentioned above, also included erroneous mentions of companies, such as Cisco, which were not involved, and mentions of companies which were involved but did not wish to be publicly disclosed at that time) we immediately reached out to the reporters to offer corrections. Unfortunately, despite our best efforts, the news spread too fast and we were unable to contain it effectively. This confusion was the last thing we wanted. It detracted from what was and remains a truly ambitious and exciting endeavor. We sincerely apologize for what may have been construed as intentional misrepresentation, and we would like to reassure the community that we will take great care to ensure our future communications convey information as clearly and precisely as possible.
Thankfully, the now more than 40 participating companies, undeterred by the commotion in the press, have continued to innovate, test, and explore the many possibilities of the Data Marketplace. We are extremely excited about this ongoing collaboration and forthcoming developments. Beginning in early 2018, we aim to publish a number of proof-of-concept applications, pilots and studies. We are very much looking forward to bringing this initiative one step closer to production applications.
DCI’s claim:
“Whether or not IOTA’s ledger is “tamper-proof,” the entire IOTA network went down in November, and was completely inoperable for about three days. That this has never happened in Bitcoin or Ethereum suggests the extent to which the IOTA network relies on the “coordinator” — a single point of failure — and is not truly decentralized.”
“Whether or not IOTA’s ledger is “tamper-proof,” the entire IOTA network went down in November, and was completely inoperable for about three days. That this has never happened in Bitcoin or Ethereum suggests the extent to which the IOTA network relies on the “coordinator” — a single point of failure — and is not truly decentralized.”
The referenced shut down actually took place in October and was related to an attack on the network which would have resulted in the loss of user funds due to continuous key reuse. At the time of the attack, the IOTA Foundation, in conjunction with the full node operators, swiftly responded by suspending operations. Once the issue was identified and resolved, a snapshot was taken to protect vulnerable addresses, the network full node operators came to a consensus on this snapshot, the Coordinator was turned back on and the network resumed normal operations. IOTA node operators, understanding the importance of the Coordinator’s role in securing the network while it is still young, voluntarily suspended operations during this time.
The purpose of the Coordinator in the infancy stage of the IOTA network has been transparently communicated throughout the history of IOTA. As the team has explained at length, the Coordinator is a temporary measure to help bootstrap the network and protect it during its infancy. Once there are enough full nodes and transactions to secure and sustain the IOTA network, the Coordinator will be permanently removed from the network. The specific reasons for this are complicated; there is a more detailed explanation on page 19 of the white paper:
“… This indicates the need for additional security measures, such as checkpoints, during the early days of a tangle-based system.”
(Emphasis added.)
“… This indicates the need for additional security measures, such as checkpoints, during the early days of a tangle-based system.”
(Emphasis added.)
It is important to bear in mind that IOTA is still extremely young compared to Bitcoin and Ethereum. Bitcoin and Ethereum both also needed additional bootstrapping while the networks were still young and vulnerable, and both have also experienced the occasional hiccup along the way. In addition, several of IOTA’s core developers have learned from personal experience that even the blockchain architecture’s overall security, vulnerability to certain sophisticated types of attacks, and long-term stability are not without their own legitimate open questions.
IOTA, like Bitcoin and Ethereum, is the “first of its kind” and we should anticipate that things will not work perfectly from the start. Fortunately, the IOTA Foundation has an excellent team, amazing community support, and is dedicated to resolving any issues that do arise as quickly as possible. It is vital to note that as any fundamentally new technology is adopted by large groups of people, new problems and unforeseen edge cases will invariably cause some hiccups along the way.
A further mistakenly identified flaw was mentioned by the DCI report:
“Also troubling, IOTA developers were able to transfer funds out of users’ IOTA accounts. The user was then required to participate in a “reclaim” process to request their funds. We believe IOTA’s developers should not have access to such funds; it’s rife with risk.”
“Also troubling, IOTA developers were able to transfer funds out of users’ IOTA accounts. The user was then required to participate in a “reclaim” process to request their funds. We believe IOTA’s developers should not have access to such funds; it’s rife with risk.”
This is a blatant mischaracterization of the situation. One of the most well-known and well-documented (e.g., here, here, and here) technical challenges with the current implementation of IOTA from a user’s perspective is the private-key reuse issue. In the IOTA GUI Wallet introductory blog post, Dominik specifically alerted users to the fact that IOTA“can be hard to grasp for newcomers, [even] for people coming from other Blockchain projects.”Due to some mathematical and technical details regarding the digital signature design chosen by IOTA for security (appreciating the very real threat posed by quantum computers to industry standard cryptography functions in the not-so-distant future), each address should have at most one outgoing transaction. Subsequent outgoing transactions from the same address make it vulnerable to theft through brute-force attacks.
The IOTA team has taken special care to educate users about these unique problems and how to avoid them. In addition to the many technical guides for using the GUI Wallet (referenced above) and an active community support group with people offering round-the-clock technical advice, the GUI Wallet itself has numerous built-in safety features such as address reuse warnings and address tracking features. Despite all of these precautions, many users were still making the mistake of signing transactions multiple times with the same private key, thereby exposing the key to a brute-force attack. As a result, these addresses became vulnerable to attack and sadly, some users indeed fell victim to hackers.
In September of this year, a significant and growing number of potentially vulnerable addresses were noted, and the IOTA team decided to take action to protect the affected addresses. This decision was not taken lightly, but rather after careful consideration of the situation at hand:
- On the one hand, it was only a matter of time before users’ addresses would be hacked and their funds would also be stolen through brute-force attacks. Sophisticated hackers around the world were undoubtedly aware of their vulnerabilities, actively working to break them, and getting closer every day.
- On the other hand, freezing user funds, even if only to protect them, violates many of the core principles of the DLT community which we also hold dear.
In the end, with the community’s best interests in mind, we decided to take drastic and protective measures to prevent further theft from IOTA token holders. Importantly, these protective measures were only possible with the direct and active support of the IOTA community.
The vast majority of IOTA node operators have a good working relationship with the IOTA Foundation and the community. They respect the Foundation leadership, and they understand the purpose of both the Coordinator, which currently secures the network against attacks in its infancy, and the regularly scheduled snapshots and software updates. Ultimately, in order to implement the preventative measures mentioned above, a special snapshot was scheduled wherein all funds vulnerable to theft were tagged with a key reuse marker. The community was then asked to independently verify this key reuse designation, and once it was verified by the community, the subsequent snapshot moved all the vulnerable balances into a new address controlled by the IOTA Foundation. The IOTA Foundation would keep the funds safe, and the owners would have the ability to reclaim them at a later date once a reclaim process was implemented (to prove ownership and handle it in an organized and efficient manner). This has since been completed (see reclaim instructions here).
This movement of funds was only possible with the full cooperation of the community and the IOTA node operators, and would not be possible for the IOTA Foundation to do unilaterally. We took great care to ensure that this entire process from start to finish was completely transparent and independently verifiable by our community, and indeed our community did independently verify it (see, for example, here, here and here).
This situation has some parallels with the Ethereum DAO hack of 2016. The Ethereum Foundation, in an effort to protect users from losing hacked funds, rewrote history and changed address balances. Undoubtedly, some Ether token holders were surprised to find out that after having provided a service or sold a product and having received payment in what they believed to be an immutable and irreversible Ether token, this was actually not the case. This rewriting of history was extremely controversial for the Ethereum community, and Ethereum Classic was born as a result. For both Ethereum and IOTA, these unfortunate situations were not the fault of the underlying technology behind them, but rather — in both cases — user error. Also in both cases, because these situations happened while the projects were still very young and vulnerable, and consequently were potentially fatal to the entire undertaking, drastic measures were taken. We know how difficult of a situation this must have been for the Ethereum Foundation, because we know how difficult it was for us.
The IOTA team and the wider IOTA community continue to work towards making all IOTA users aware of the address reuse vulnerability, and to educate users about how to safely perform IOTA transactions. We have chosen not to change the digital signature design because while traditional cryptography’s vulnerability to quantum computers is permanent, the address reuse vulnerability can and will be mitigated by a better engineered wallet. New safety features on the current wallet have been since introduced (see below) and the IOTA team is hard at work developing a user-friendly solution to this problem to prevent unintentional misuse from occurring altogether — which is not at all a trivial task.
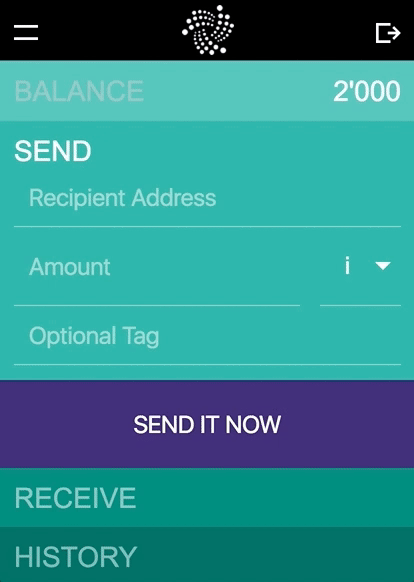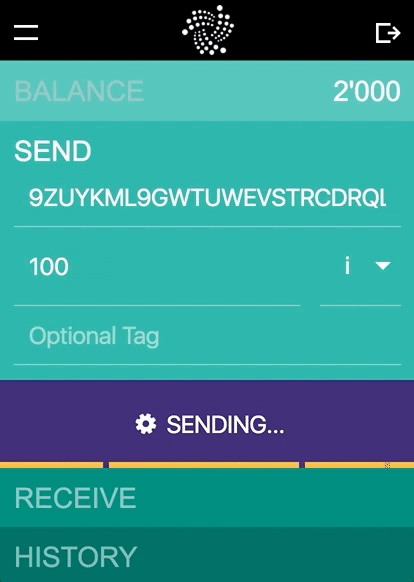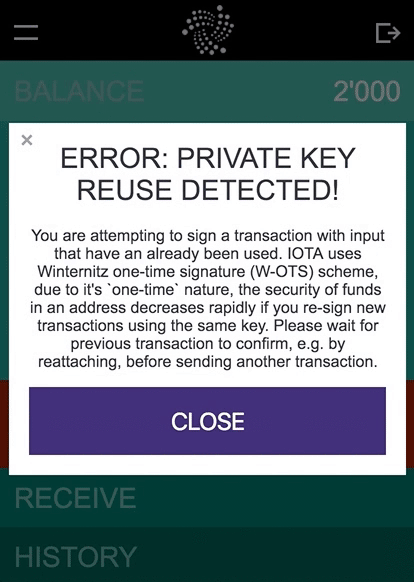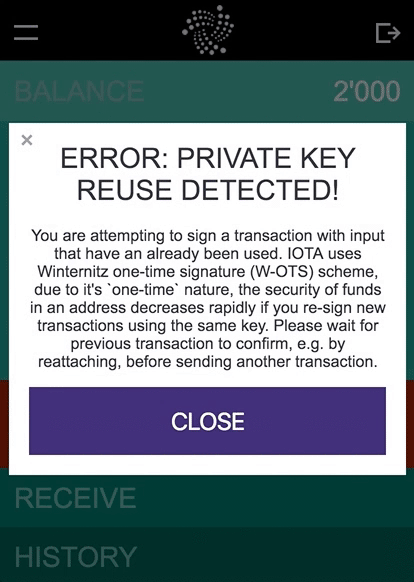
We appreciate the support from the IOTA community through this unfortunate situation, and hope those users who had their funds moved to an IOTA controlled address understand that we made our decision only after careful consideration and with only the intention of protecting those funds from theft.
In the interest of answering the DCI’s claim comprehensively, we say this: the IOTA Foundation does not have any technical means to access funds apart from the full cooperation of the community and the node operators, and the decision to move funds was taken solely out of care and concern for the community. While we regret that this difficult situation arose, we believe we made the right decision in light of all the facts and circumstances.
In our final article of this mini-series, we discuss in detail the remainder of the points raised in the DCI’s reports and examine the deeper, underlying issues.
This is a multi-part post. Links to the other parts can be found below:
Part 1
Part 2
Part 3 (this article)
Part 4